Introduction to Security Reduction: A Comprehensive Guide to Enhancing Cyber Resilience

In the ever-evolving landscape of cyber security, organizations face the daunting challenge of protecting their sensitive data and infrastructure from a multitude of threats. Security reduction emerges as a crucial strategy to proactively identify and mitigate vulnerabilities that could potentially compromise systems and networks. This in-depth guide delves into the intricacies of security reduction, empowering readers with the knowledge and techniques to safeguard their digital assets.
5 out of 5
| Language | : | English |
| File size | : | 5130 KB |
| Print length | : | 268 pages |
Chapter 1: Understanding the Landscape of Security Reduction
This chapter provides a foundational understanding of security reduction, defining its key concepts, scope, and significance within the broader realm of cyber security. Readers will gain insights into the various types of vulnerabilities, including software flaws, configuration errors, and human vulnerabilities, that can leave systems exposed to exploitation.
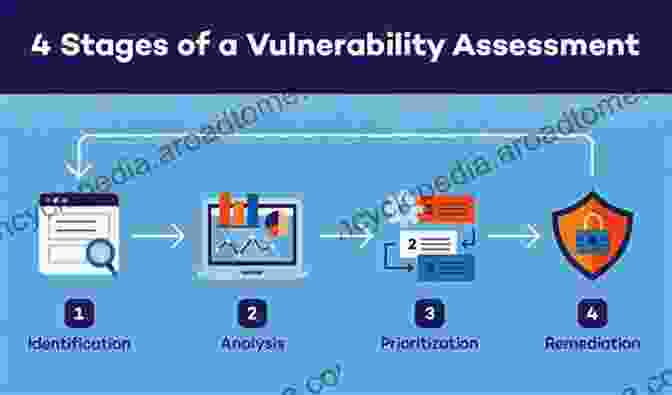
Chapter 2: Vulnerability Assessment: Uncovering System Weaknesses
Vulnerability assessment plays a pivotal role in security reduction, enabling organizations to identify and prioritize the weaknesses that could be exploited by attackers. This chapter delves into the various techniques used for vulnerability assessment, such as automated scanning, manual testing, and source code review. Readers will learn how to effectively scan systems for known vulnerabilities, analyze the severity of findings, and prioritize remediation efforts.
- Automated Scanning: Utilizing tools to automate vulnerability detection and identification.
- Manual Testing: Conducting thorough manual inspections to uncover vulnerabilities that automated scans may miss.
- Source Code Review: Examining the underlying codebase to identify potential vulnerabilities and security flaws.
Chapter 3: Penetration Testing: Simulating Real-World Attacks
Penetration testing takes vulnerability assessment a step further by simulating real-world attacks to evaluate the effectiveness of security controls. This chapter provides practical guidance on planning, executing, and reporting penetration tests. Readers will learn how to identify and exploit vulnerabilities, assess the impact of potential breaches, and develop effective countermeasures to mitigate risks.

Chapter 4: Countermeasures: Mitigating Vulnerabilities and Enhancing Resilience
Effective security reduction involves implementing appropriate countermeasures to mitigate identified vulnerabilities and enhance the overall security posture of systems. This chapter explores a comprehensive range of countermeasures, including patching, configuration hardening, access control, and network segmentation. Readers will learn how to select and implement appropriate countermeasures based on the specific vulnerabilities and risks faced by their organizations.
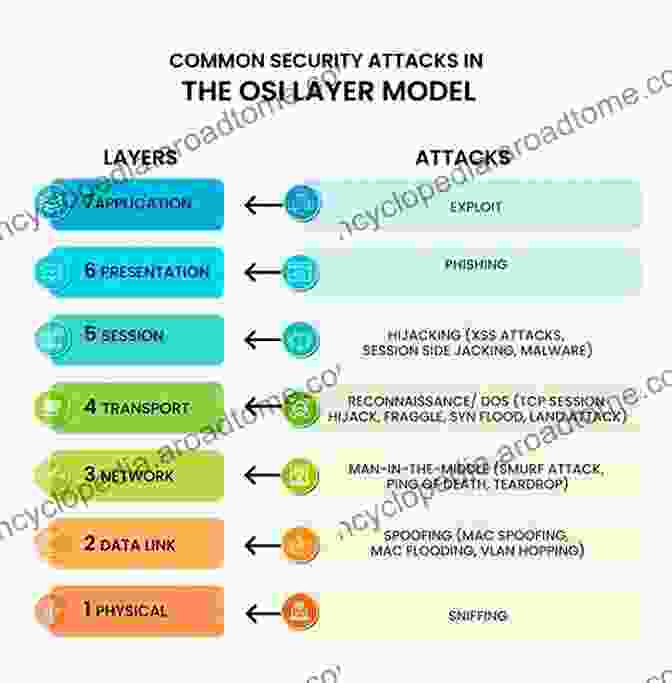
Chapter 5: Case Studies and Best Practices
To illustrate the practical application of security reduction techniques, this chapter presents real-world case studies that showcase successful implementations in different industries. Readers will gain valuable insights into how organizations have successfully reduced their security risks, implemented effective countermeasures, and improved their overall cyber resilience.
Mastering the art of security reduction is essential for organizations seeking to protect their sensitive data and infrastructure from the ever-evolving threat landscape. This comprehensive guide has equipped readers with a deep understanding of vulnerability assessment, penetration testing, and countermeasures, empowering them to proactively identify and mitigate risks, and enhance the overall security posture of their systems. By embracing the principles and techniques outlined in this guide, organizations can significantly reduce their exposure to cyber attacks and safeguard their valuable assets.
5 out of 5
| Language | : | English |
| File size | : | 5130 KB |
| Print length | : | 268 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Lou Jacobs
Lou Jacobs Saludable Mente
Saludable Mente Meredith O Brien
Meredith O Brien Karina Yan Glaser
Karina Yan Glaser 16th Edition Kindle Edition
16th Edition Kindle Edition Joseph Rogers
Joseph Rogers Deborah M Shlian
Deborah M Shlian 1992nd Edition Kindle Edition
1992nd Edition Kindle Edition Ben Mezrich
Ben Mezrich Danny Rubin
Danny Rubin 1st Ed 2016 Edition
1st Ed 2016 Edition Di Drinkwater
Di Drinkwater David Head
David Head John M Deutch
John M Deutch Martin Heidegger
Martin Heidegger Dani Jessant
Dani Jessant Elsie Callender
Elsie Callender Maria Liberati
Maria Liberati Thomas H Ward
Thomas H Ward Norine Dresser
Norine Dresser
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Edmund HayesMitochondrial Dynamics in Cardiovascular Medicine: Advances in Experimental...
Edmund HayesMitochondrial Dynamics in Cardiovascular Medicine: Advances in Experimental... Gordon CoxFollow ·2.5k
Gordon CoxFollow ·2.5k Brody PowellFollow ·2.2k
Brody PowellFollow ·2.2k John GrishamFollow ·11.7k
John GrishamFollow ·11.7k Easton PowellFollow ·7k
Easton PowellFollow ·7k Gene PowellFollow ·5.3k
Gene PowellFollow ·5.3k Victor HugoFollow ·10.1k
Victor HugoFollow ·10.1k Chad PriceFollow ·14.2k
Chad PriceFollow ·14.2k Jackson HayesFollow ·9k
Jackson HayesFollow ·9k

 Desmond Foster
Desmond FosterBreak Free from the Obesity Pattern: A Revolutionary...
Obesity is a global pandemic affecting...

 Jared Nelson
Jared NelsonRobot World Cup XXIII: The Ultimate Guide to Advanced...
The Robot World Cup XXIII: Lecture Notes in...

 Charlie Scott
Charlie ScottFirst International Conference TMM CH 2024 Athens...
Prepare for...

 Finn Cox
Finn CoxRe-Capturing the Conversation about Hearing Loss and...
Challenging...

 Camden Mitchell
Camden MitchellJourney into the Realm of Digital Systems: An Immersive...
In the ever-evolving technological...

 Javier Bell
Javier BellUnveiling the Toxins Behind Multiple Sclerosis: A...
Multiple sclerosis...
5 out of 5
| Language | : | English |
| File size | : | 5130 KB |
| Print length | : | 268 pages |